Posts
Below are the steps of how to fix the banner (version information) in IIS 8.0/8.5
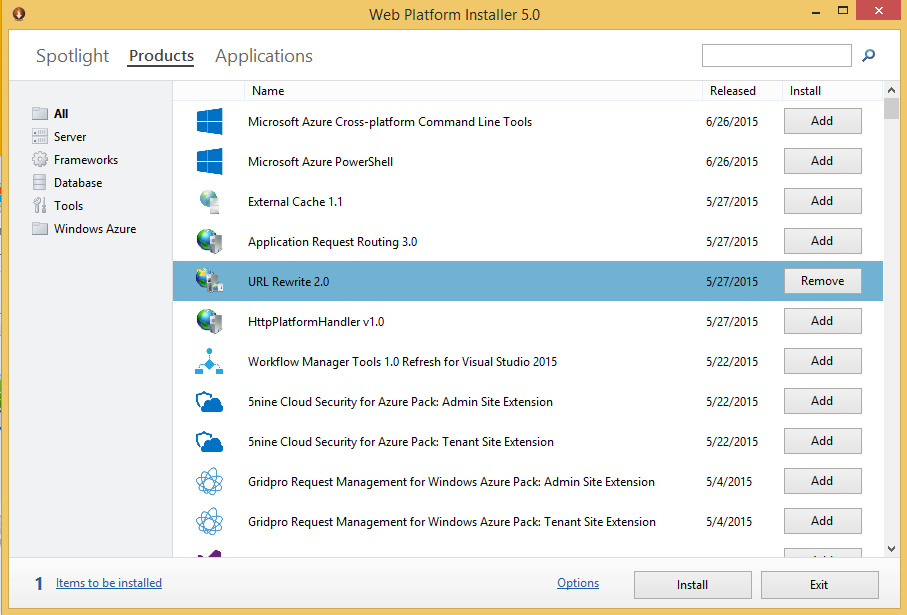
Step 1:
Install the latest version of Microsoft Web Platform Installer (https://www.microsoft.com/web/downloads/platform.aspx/).
Step 2:
Install URL Rewrite 2.0 using Web Platform Installer on the server.
This article presents the key risks with DirectAccess and how to audit them.
Let’s begin by first understanding the DirectAccess technology
Introduction of DirectAccess
DirectAccess, also known as Unified Remote Access, is a VPN-like technology that provides intranet connectivity to client computers when they are connected to the Internet.
Direct Access overcomes the limitations of VPNs by automatically establishing a bi-directional connection from client computers to the corporate network so users never have to think about connecting to the enterprise network and IT administrators can manage remote computers outside the office, even when the computers are not connected to the VPN.
When a DirectAccess client is outside of the corporate network and has an active Internet connection, the client will attempt to establish connectivity with the DirectAccess gateway by creating IPsec tunnels defined by the connection security rules in the Windows Firewall on the client.
How does the DirectAccess Server work?
- The DirectAccess client connects to a publicly exposed Active Directory, which then checks for DirectAccess policy and then allows the client to connect to the DirectAccess server.
- The DirectAccess server checks whether the Windows firewall is enabled or not. If not it will not allow the client to connect.
- After connecting, the DirectAccess server will allow the user to connect to Intranet servers like Application server, Mail Server, etc.
Hi all,
Recently i have found Insecure Direct Object Issue on Nokia. I have already reported this issue and also got fixed.
Thanks to Nokia developer Team. They have listed my name on Nokia Hall Of Fame List on below mentioned URL:
http://www.nokia.com/global/security/acknowledgements/

Before we start discussing the issue we will first look into what Insecure Direct Object Reference is?
What is Insecure Direct Object Reference?
The Insecure Direct Object References represent the flaws in system design where access to sensitive data/assets is not fully protected and data objects are exposed by application with assumption that user will always follow the application rules.
Insecure Direct Object Reference is an attack where attacker who is an authenticated system user, simply changes a parameter value that directly refers to a system object or another object the user isn’t authorized for.
(Note:
***Authentication:***Authentication verifies who you are.
Authorization: Authorization verifies what you are authorized to do. )